Fission Stories #151
In July 2013, the NRC submitted to the U.S. Congress an annual report on nuclear power plant security during 2012.
On the plus side, no nuclear power plant was stolen last year.
On the down side, one nuclear power plant was destroyed during a simulated attack last year.
Every three years, the NRC monitors force-on-force testing at each nuclear plant. In other words, about one-third of the U.S. nuclear plants undergo force-on-force testing each year. The force-on-force tests derive their name from at least two exercises pitting a small group of mock attackers (called the Composite Adversary Force) against the plant’s security measures (e.g., intrusion detection systems, locked doors, and armed responders). The mock attackers seek to simulate the destruction of all components on a Target Set—the minimum list of equipment that, when disabled, causes radioactivity to be released from the reactor core or spent fuel pool. The armed responders seek to prevent the mock attackers from achieving that goal.
The NRC contacts the nuclear plant’s owner about six weeks in advance to reserve a date and time for the mock attacks. This advance notice does take some of the “surprise” out of the “surprise attack,” but it is necessary. During force-on-force tests, the plant owner must provide two separate sets of security officers—one to defend the facility from the mock attackers and the second to defend the facility from real attackers.
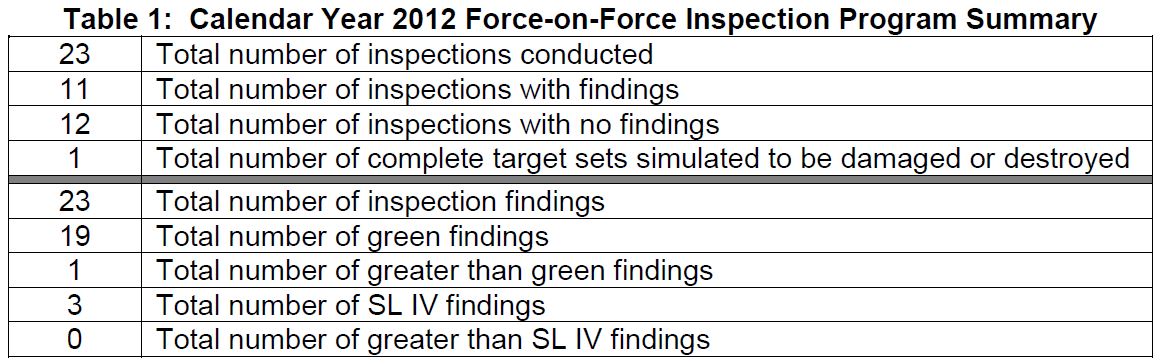
The NRC monitored force-on-force tests at 23 nuclear plants in 2012:
Table 1 comes from the NRC’s annual report to Congress. It indicates that at 12 plants, or slightly over half of those tested last year, the force-on-force tests resulted in “no findings.” (Actually, this means there were “no bad findings” in that the NRC “found” that security at these dozen plants successfully defended against all simulated attacks—a very good thing.
Table 1 also indicates that the NRC identified 23 findings at 11 plants during force-on-force testing in 2012—an average of about two findings per plant. While the specific nature of the findings has not been disclosed by the NRC, past results suggest that they can include problems like an armed responder taking the wrong route or arriving too late when directed to an interdiction position.
During one force-on-force exercise during 2012, the mock attackers simulated the destruction of every item on the Target Set—in other words, they successfully sabotaged the plant.
The NRC has not publicly disclosed the identity of the plant experiencing the force-on-force test failure. Had it been a real attack, the identity would likely be all too well known.
Our Takeaway
Some 23 force-on-force tests were conducted by the NRC at U.S. nuclear plants last year. Each test consisted of at least two force-on-force exercises. The single failure among at least 46 exercises means that nuclear plant security measures were about 98% successful last year. That’s a high score on a school student’s exam or on a test for a driver’s license. But it may but be high enough when the other 2% involves nuclear disaster.
And what if real attackers didn’t call ahead to politely schedule the date and time for their arrival.
And what if real attackers didn’t politely limit their numbers to a relatively small group so as to literally give the security guards a fighting chance?
Would the 98% success rate drop if real attackers weren’t so considerate?
But there is a silver lining, perhaps two, in the NRC’s report. First, that one force-on-force exercise resulted in simulated sabotage speaks to the value of the tests. If all exercises at all plants always resulted in defeat of the mock attackers, one might suspect that the exercises were little more than animated answers to “who’s buried in Grant’s tomb?” questions.
Second, all security weaknesses identified during the simulated attacks can be fixed before being exploited during real attacks.
“Fission Stories” is a weekly feature by Dave Lochbaum. For more information on nuclear power safety, see the nuclear safety section of UCS’s website and our interactive map, the Nuclear Power Information Tracker.