There has been considerable media coverage recently about alleged hacking into computer systems at or for U.S. nuclear power plants. The good news is that the Nuclear Regulatory Commission (NRC) and the nuclear industry are not merely reacting to this news and playing catch-up to the cyber threat. The NRC included cyber security protective measures among the regulatory requirements it imposed on the nuclear industry in the wake of 9/11. The hacking reported to date seems to have involved non-critical systems at nuclear plants as explained below.
The bad news is that there are bad people out there trying to do bad things to good people. We are better protected against cyber attacks than we were 15 years ago, but are not invulnerable to them.
Nuclear Plant Cyber Security History
The NRC has long had regulations in place requiring that nuclear plant owners take steps to protect their facilities from sabotage by a small group of intruders and/or an insider. After 9/11, the NRC issued a series of orders mandating upgrades to the security requirements. An order issued in February 2002 included measures intended to address cyber security vulnerabilities. An order issued in April 2003 established cyber attack characteristics that the NRC required owners to protect against.
The orders imposed regulatory requirements for cyber security on nuclear plant owners. To help the owners better understand the agency’s expectations for what it took to comply with the requirements, the NRC issued NUREG/CR-6847, “Cyber Security Self-Assessment Method for U.S. Nuclear Power Plants,” in October 2004; Regulatory Guide 5.71, “Cyber Security Programs for Nuclear Facilities,” in January 2010; NUREG/CR-7117, “Secure Network Design,” in June 2012; and NUREG/CR-7141, “The U.S. Nuclear Regulatory Commission’s Cyber Security Regulatory Framework for Nuclear Power Reactors,” in November 2014. In parallel, the Nuclear Energy Institute developed NEI-08-09, “Cyber Security Plan for Nuclear Power Reactors,” in April 2010 that the NRC formally endorsed as an acceptable means for conforming to the cyber security regulatory requirements.
First Step: NANA
Anyone who has read more than one report about the U.S. nuclear power industry will appreciate that NANA was a key step in the road to cyber security regulations—Need A New Acronym. The nuclear industry and its regulator need to be able to talk in public without any chance of the public following the conversation, so acronyms are essential elements of the nukespeak. Many FTEs (full-time equivalents, or NRC person-hours) went into the search for the new acronym, but the effort yielded CDA—Critical Digital Assets. It was a perfect choice. Even if one decoded the acronym, the words don’t give away much about what the heck it means.
Finding CDA Among the NCDA, CAA, and NCAA
Armed with the perfect acronym, the next step involved distinguishing CDA from non-critical digital assets (NCDA), critical analog assets (CAA), and non-critical analog assets (NCAA, sorry college sports enthusiasts). Doing so is an easy three-step process.
Step 1: Inventory the Plant’s Digital Assets
The NRC bins the digital assets at a nuclear power plant into the six categories shown in Figure 1. Security systems include the computers that control access to vital areas within the plant, sensors that detect unauthorized entries, and cameras that monitor restricted areas. Business systems include the computers that enable workers to access PDFs of procedures, manuals, and engineering reports. Emergency preparedness systems include the digital equipment used to notify offsite officials of conditions at the plant. Data acquisition systems include sensors monitoring plant parameters and the equipment relaying that information to gauges and indicators in the control room as well as to the plant process computer. Safety systems could include the equipment detecting high temperatures or smoke and automatically initiate fire suppression systems. Control systems include process controllers that govern the operation of the main turbine or regulate the rate of feedwater flow to the steam generators (pressurized water reactors) or reactor pressure vessels (boiling water reactors). The first step has owners inventorying the digital assets at their nuclear power plants.
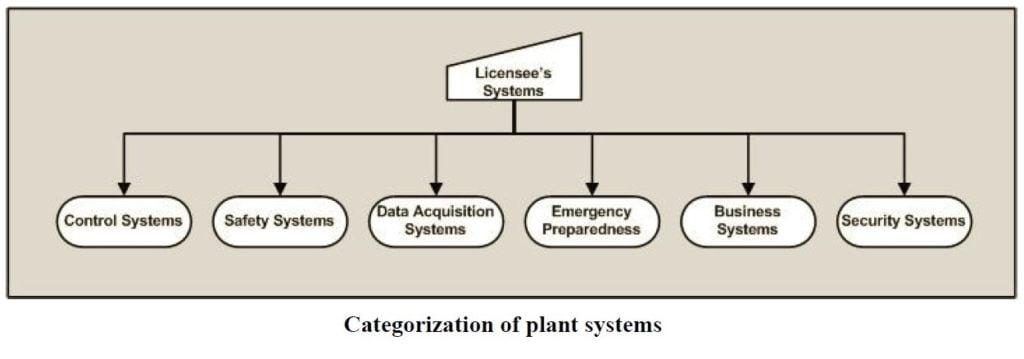
Fig.1 (Source: Nuclear Regulatory Commission)
Step 2: Screen Out the Non-Critical Systems, Screen in the Critical Systems
Figure 2 illustrates the evaluations performed for the inventory of digital assets assembled in Step 1 to determine which systems are critical. The first decision involves whether the digital asset performs a safety, security, or emergency preparedness (SSEP) function. If not, the evaluation then determines whether the digital asset affects, supports, or protects a critical system. If the answer to any question is yes, the digital asset is a critical system. If all the answers are no, the digital asset is a non-critical system.
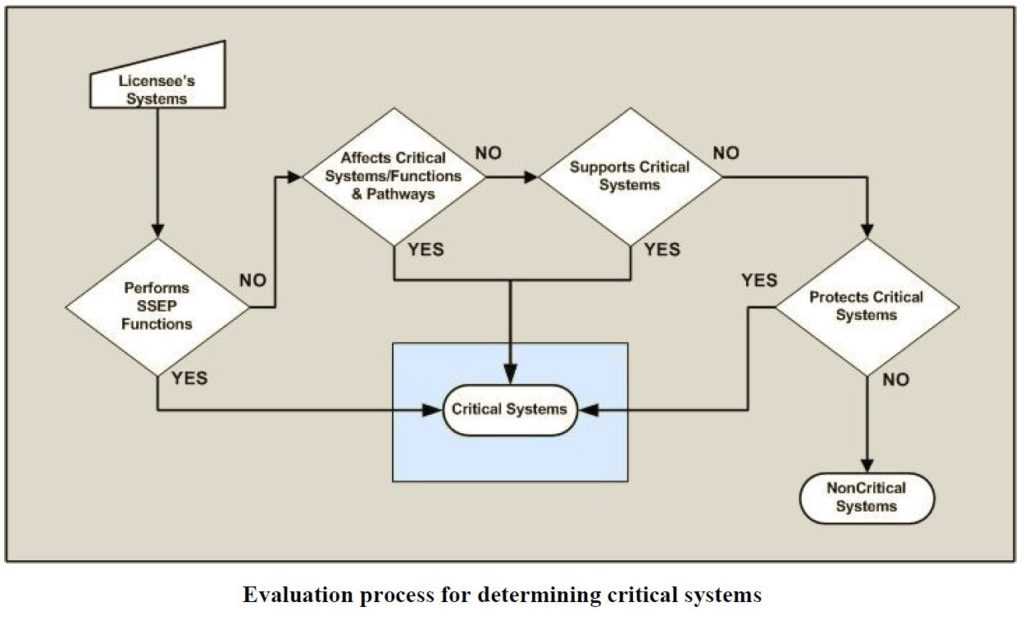
Fig. 2 (Source: Nuclear Regulatory Commission)
Step 3: Screen Out the NCDA, Screen in the CDA
Figure 3 illustrates the evaluations performed for the inventory of critical systems identified in Step 2 to determine which are critical digital assets. The first decision involves whether the critical system performs a safety, security, or emergency preparedness (SSEP) function. If not, the evaluation determines whether the critical system affects, supports, or protects a critical asset. If the answer to any question is yes, the critical system is a critical digital asset. If all the answers are no, the critical system is a non-critical digital asset.
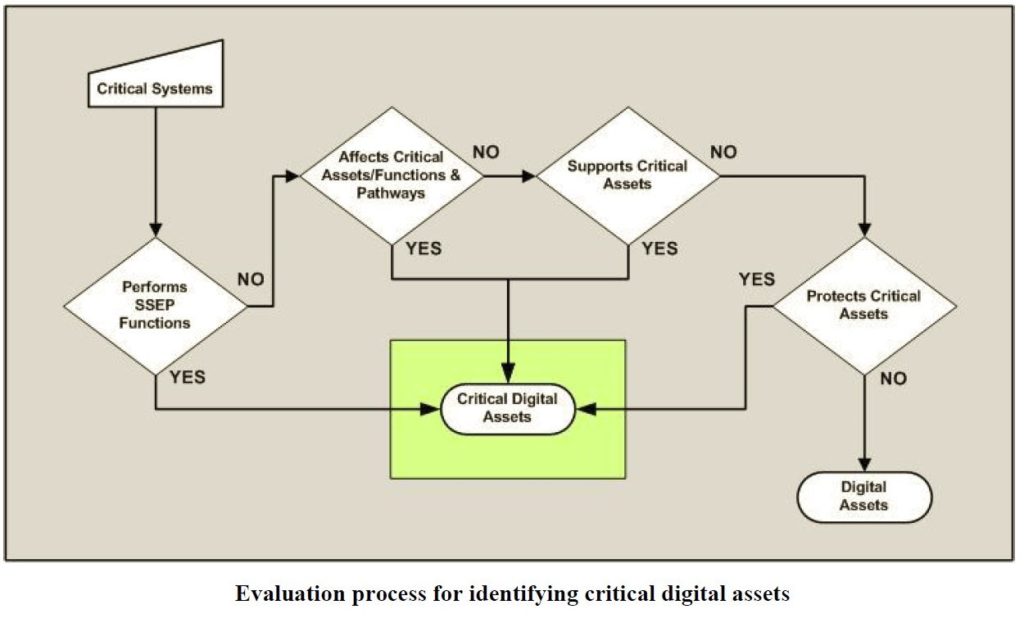
Fig. 3 (Source: Nuclear Regulatory Commission)
Remaining Steps
Once the CDAs are identified, the NRC requires that owners use defense-in-depth strategies to protect workers and the public from harm caused by a cyber-based attack. The defense-in-depth protective layers are:
- Prompt detection and response to a cyber-based attack
- Mitigating the adverse consequences of a cyber-based attack
- Restoring CDAs affected by a cyber-based attack
- Correcting vulnerabilities exploited by a cyber-based attack
The Power of One (Bad Person)
The NRC instituted cyber security regulatory requirements many years ago. The NRC’s inspectors have assessed how effectively measures undertaken by plant owners conform to these requirements. Thus, the U.S. nuclear industry does not have to quickly develop protections against cyber attacks in response to recent reports of hacking and attacking. The job instead is to ensure required protections remain in place as effectively as possible.
Unfortunately, digital technology can also broaden the potential harm caused by an insider. The NRC’s security regulations have long recognized that an insider might attempt sabotage alone or in conjunction with unauthorized intruders. In what the military terms a “force multiplier,” digital technology could enable the insider to attack multiple CDAs. The insider could also supply passwords to the outside bad guys, saving them the trouble of hacking and the risk of detection.
The hacking of computer systems by outsiders made news. The mis-use of CDAs by an insider can make for grim headlines.