Disaster by Design/ Safety by Intent #60
Security by Intent
Nuclear Energy Activist Toolkits #32 and #47 described the emergency plan preparations required by federal regulations for every operating nuclear power plant. Other federal regulations require design features backed by testing and inspection protocols intended to minimize the chances of a nuclear plant accident that might result in the emergency plans being needed. That’s Safety by Intent.
The necessary companion is Security by Intent. The string of equipment malfunctions and worker miscues that could trigger a nuclear accident could also be pulled intentionally. Federal regulations seek to minimize the chances of a nuclear plant accident being triggered by sabotage.
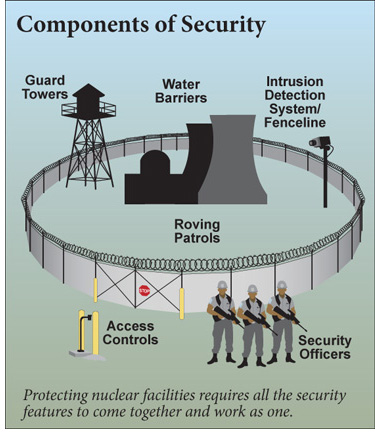
Fig. 1 (Source: Nuclear Regulatory Commission)
The regulations protect against sabotage by people working at the plant and/or people breaking into the plant. After 9/11, the NRC revised the regulations to better protect against sabotage by insiders. Prior to 9/11, individuals could freely enter the security fences around a nuclear plant only after background checks revealed no criminal or trustworthiness histories. After 9/11, the NRC revised its regulations to require that the background checks be periodically revisited to ensure that the initial determinations remained valid.
The NRC also revised its regulations after 9/11 to better protect against sabotage by outsiders. Prior to 9/11, the regulations required protection against a modest number of outside attackers. After 9/11, the NRC revised its regulations to increase the number of potential attackers. In addition, the revised regulations assume the attackers may use more challenging tactics and more harmful weapons.
The revised regulations also upped the training and qualification requirements for security force personnel, which resulted in better protection against sabotage by insiders and outsiders.
Testing Security
Prior to 9/11, the NRC determined how effectively the various security elements (e.g., intrusion detection system, locked doors to areas housing vital equipment, defensive positions by security officers, etc.) fit together to deter sabotage through force-on-force tests that pitted mock attackers against the plant’s gates, guards, and guns. Real bullets were not used, so the tests employed people (controllers) who would judge who had yelled “Bang!” first. The controllers introduced delays as the players awaited rulings on who continued the fight and who retired to the sidelines. The security at each operating nuclear plant was checked by a force-on-force test about once every eight years.
After 9/11, the NRC increased the frequency and realism of the force-on-force tests. Each operating plant gets a force-on-force test about once every three years. And while the participants still don’t use real bullets, they use laser guns that provide more accurate and timely resolution of who-shot-whom questions.
Seeing a Security Problem
The passive defense provided by security fences around nuclear power plants is backed by active monitoring. Intrusion detection systems warn onsite security force personnel about unauthorized persons climbing over or cutting through a fence. The security force personnel can focus cameras to see whether a near-sighted deer wandered into the fence, a lazy bird landed on it, or ne’er do wells are entering the site sans invitation. Security force personnel need to discern foe from fawn to decide how to respond properly.
The periodic security checks conducted by the NRC included holding up cards at various spots along the fences to evaluate how good the cameras could “see” under various lighting and weather conditions—much like the eye-charts used by optometrists to check on their patients’ visual acuity. The NRC wanted to know if sun glare, darkness, fog or other factors could mask a section of the fence and take longer for security force personnel to detect intruders.
The NRC inspectors used the same small set of cards during these camera checks at the plants. Like memorizing the lines on an eye-chart, security folks at the plants communicated the symbols on the NRC’s card deck to the people monitoring the cameras. The question for the monitors changed from “what do you see?” to “does what you see look more like x, y, or z?”
The NRC figured out the game, too. They changed their card deck without telling the plant owners. The game was up the first time a monitor reporting seeing a symbol from the discarded card deck.
Evolving Security Measures
The NRC extensively revised its regulations and oversight practices after 9/11 to provide better protection against nuclear plant sabotage. But the NRC had made changes to security regulations and practices before 9/11 and has made further changes since the 9/11 revisions. The hazard environment evolves as new threats emerge and more harmful weapons are developed. The NRC strives to minimize the gap between evolving hazards and defenses against them.
Disaster by Design
Some reasonable and informed individuals contend that more should be done to improve nuclear plant security. It is undeniable that doubling the size of the guard force or installing an additional fence around the existing ones would make it harder to sabotage a nuclear plant.
Other equally reasonable and informed individuals contend that the post-9/11 security measures are more than sufficient and, with international terrorists preoccupied with other targets, it might be time to lessen some of the more costly security measures.
When the overwhelming majority of reasonable and informed individuals felt that security measures were more than adequate, it is time to slash here and there.
When the overwhelming majority of reasonable and informed individuals felt that security measures were woefully inadequate, it is time to beef up there and here.
When a sizeable subset of reasonable and informed individuals feel that existing security measures are overkill and another sizeable subset feel that much more must be done, it is time for case-by-case actions to plug gaps while removing unwarranted extraneous aspects.
I know which camp UCS is in and know many fellow campers. But I also know several people in the camp down the road. It therefore seems a bad time to slash and not a good time for beefing up. But it seems a swell time to shift security surpluses to seal shortcomings (and schedule a spectacular shindig with any surviving savings.)
—–
UCS’s Disaster by Design/ Safety by Intent series of blog posts is intended to help readers understand how a seemingly unrelated assortment of minor problems can coalesce to cause disaster and how effective defense-in-depth can lessen both the number of pre-existing problems and the chances they team up.
Featured photo: NRC